Cloud computing simply implies using a network of remote servers hosted on the
Internet to store, manage, and process data, rather than a local server
or a personal computer.
Cloud computing models;
Public cloud (off-site and remote) describes cloud computing where
resources are dynamically provisioned on an on-demand, self-service basis over
the Internet, via web applications/web services, open API, from a third-party provider who bills on a
utility computing basis. 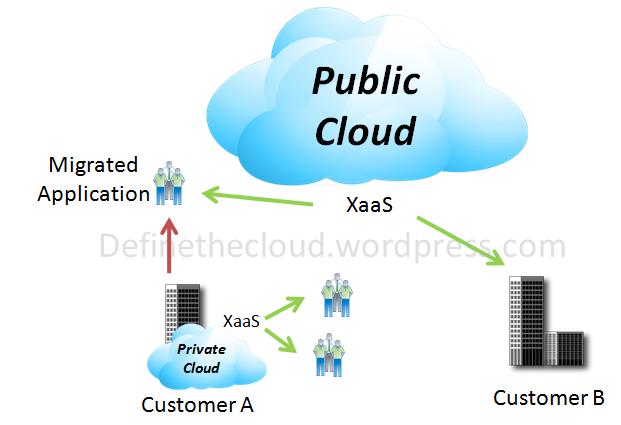


A private
cloud environment is often
the first step for a corporation prior to adopting a public cloud initiative.
Corporations have discovered the benefits of consolidating shared services on
virtualized hardware deployed from a primary datacenter to serve local and remote
users.
A hybrid
cloud environment consists
of some portion of computing resources on-site (on premise) and off-site (public
cloud). By integrating
public cloud services, users can leverage cloud solutions for specific
functions that are too costly to maintain on-premise such as virtual server
disaster recovery, backups and test/development environments.
A community
cloud is formed when
several organizations with similar requirements share common infrastructure.
Costs are spread over fewer users than a public cloud but more than a
single tenant.
What is Cloud Computing Security? - is the set of
control-based technologies and policies designed to adhere to regulatory
compliance rules and protect information, data applications and
infrastructure associated with cloud computing use.
Threats to Cloud Computing Security
Data breaches - If a multitenant cloud service database isn't designed properly, a
single flaw in one client's application could allow an attacker to get
at not just that client's data, but every other clients' data as well. You could encrypt your data to reduce the impact of a breach, but if you
lose your encryption key, you'll lose your data. However, if you opt to
keep offline backups of your data to reduce data loss, you increase
your exposure to data breaches.
Data Loss- A malicious hacker might delete a target's data out of spite, but
then, you could lose your data to a careless cloud service provider or a
disaster, such as a fire, flood, or earthquake. Encrypting your data to ward off theft can backfire if you lose your encryption key.
Account or service traffic hijacking- If an attacker gains access to your credentials, he or she can eavesdrop
on your activities and transactions, manipulate data, return falsified
information, and redirect your clients to illegitimate sites. From here, they may leverage the power of your reputation to launch subsequent attacks.
Insecure interfaces and APIs - IT admins rely on interfaces for cloud provisioning, management,
orchestration, and monitoring. APIs are integral to security and
availability of general cloud services. From there, organizations and
third parties are known to build on these interfaces, injecting add-on
services. This introduces the complexity of the new layered API; it
also increases risk, as organizations may be required to relinquish
their credentials to third parties in order to enable their agency. Weak interfaces and APIs can expose an organization to such security
issues pertaining to confidentiality, integrity, availability, and
accountability.
Denial of service - It becomes more problematic in the age of cloud computing when
organizations are dependent on the 24/7 availability of one or more
services. Denial of Service outages can cost service providers customers and prove
pricey to customers who are billed based on compute cycles and disk
space consumed. While an attacker may not succeed in knocking out a
service entirely, he or she "may still cause it to consume so much
processing time that it becomes too expensive for you to run and you'll
be forced to take it down yourself.
Malicious insiders- Can be a current or former employee, a contractor, or a business partner
who gains access to a network, system, or data for malicious purposes.
In an improperly designed cloud scenario, a malicious insider can wreak
even greater havoc. The malicious insider has increasing levels of access to more critical
systems and eventually to data. In situations where a cloud service
provider is solely responsible for security, the risk is great. Even if
encryption is implement, if the keys are not kept with the customer and
are only available at data-usage time, the system is still vulnerable
to malicious insider attack.
Cloud abuse- a bad guy using a cloud service to break an encryption key too difficult
to crack on a standard computer. Another example might be a malicious
hacker using cloud servers to launch a Denial of Service attack, propagate malware,
or share pirated software. The challenge here is for cloud providers to
define what constitutes abuse and to determine the best processes for
identify it.
Openness: IT needs to look for cloud technologies that are open in areas such as adherence to industry standards. They need to also find compliance and security solutions capable of integrating with one another so that trust in the cloud is established.
Get a grip on your data: With information flowing more freely than ever in today’s digital economy, tracking sensitive data becomes an increasingly difficult task. Get familiar with data-centric security tools that work in and outside the company’s walls, in particular, cloud data encryption and tokenization.
Test: Testing for network, logical and architectural security risks will be a very important strategy. Security testing in the cloud does change things, but it’s not impossible,It’s important to plan ahead, to communicate the changes in your test strategy, and to set appropriate expectations with your management. Above all, it is critical to communicate before and during your testing – primarily with your cloud provider, but also with your IT and security organizations.
Back it up: Having backups of your data is always a good idea whether it is stored in the cloud or not.
Use more than one cloud service: A multi-cloud strategy minimizes the risk of widespread data loss or downtime due to a localized component failure in a cloud-computing environment. Develop a security platform that allows the business to implement consistent data protection policies across multiple cloud services, preferably one that does not involve complex key management or policy administration.
Educate employees on security: People, processes and technology all need to play critical roles in ensuring adequate safeguards are in place. Proactive steps can be taken to avoid costly mistakes.
Establish comprehensive data governance policies: Governance needs to be clearly established and policies need to be put in place to ensure compliance with internal and external data privacy mandates. Data should be classified based on sensitivity and the correct data security techniques need to be applied to each class of data.
Implement data security services: Consider offering security services such as “encryption-as-a-service” or “tokenization-as-a-service” to business units within the enterprise to enable compliant cloud use/adoption while protecting data being processed and stored in the cloud.
Do encryption right: Do not store encryption keys in the software where you store your data. IT teams need to keep physical ownership of encryption keys as well as vet the strength of the encryption techniques being used.
Author - Mr. Benson Gicharu (C.E.O -Info-Tech Solutions)
